USE-CASE
Successfully Adopting Kubernetes in the Enterprise
See how you can simplify and accelerate Kubernetes adoption with DKP
K8s Adoption
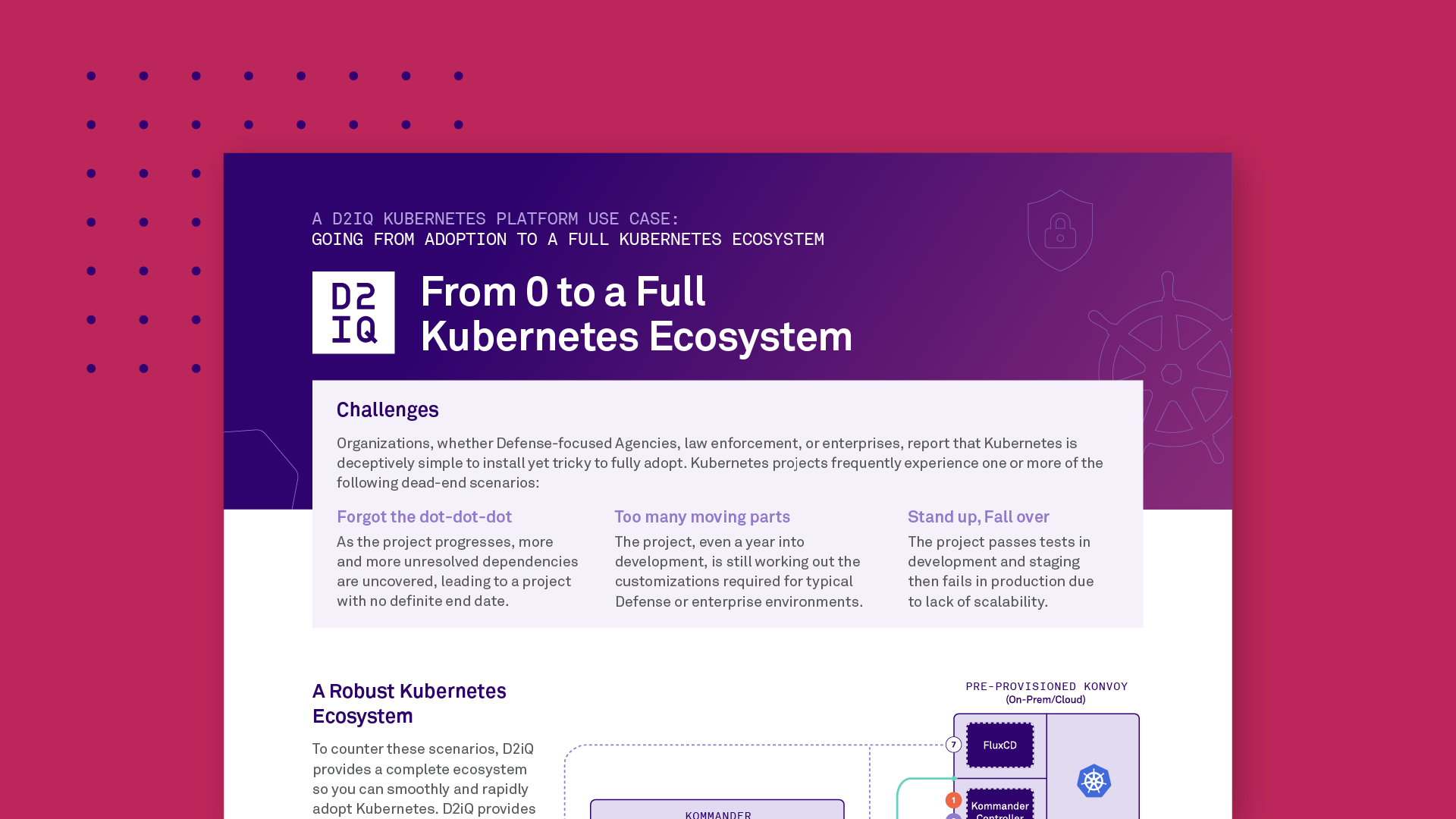
D2iQ’s product line, built-in integrations, and services provide a robust and flexible Kubernetes Ecosystem spanning on-premises, private cloud, and multiple public clouds. While covering all the dependencies for the ecosystem, D2iQ requires only configurations not customizations due to built-in routines and automation.
Benefits of Kubernetes Adoption
Portability and Flexibility
Unlike other orchestrators that are tied to a particular infrastructure, Kubernetes is highly portable because it works with virtually any type of underlying infrastructure, whether it’s on-premise, in a private cloud, public cloud, or any combination of them. It can run workloads across physical machines, private cloud, and the public cloud.
Scalability and Resource Utilization
With Kubernetes, you can automatically adjust the servers or machines required to run a service, as well as the compute power required to run a service. This means that you can scale down resources when capacity is not needed, and scale up resources when there is a greater demand, allowing for better resource utilization.
Open-Source Interoperability
Because Kubernetes is open-source, organizations can take advantage of other open-source technologies from the cloud-native landscape, such as databases, developer tools, or other services for new application needs. These open-source technologies are designed to work with Kubernetes without being locked-in to a closed-source or proprietary system so developers can quickly start prototyping, building, and deploying new digital services.
Challenges of Kubernetes Adoption
Centralized Visibility and Management
In adopting Kubernetes, admins need consistent ways to monitor multiple clusters and infrastructures at scale in order to effectively manage capacity and overall spend. However, various projects and teams are adopting a wide range of approaches to using Kubernetes without any central overarching visibility into the clusters you are monitoring, resulting in inconsistent performance and reliability issues, as well as an increase in security risks and development and maintenance costs.


Configuration Management
As your organization expands its usage of Kubernetes, clusters and services will exist in different pockets each with differing configurations in their usage, making it incredibly challenging to simplify and create consistency across organizational clusters. And if there are dozens of potential software versions in use, it may introduce vulnerabilities and security threats.
Application and Cluster Lifecycle Management
Manual deployments are time-consuming and require significant engineering effort. And when overseeing a large deployment, it’s easy to make mistakes. A lack of communication can easily cause deployments to fail and lead to rework and considerable delays in production, especially when working on large development teams that are spread across many different time zones.


Multi-Cluster Scalability
Having to manually provision and later scale down resources every time a condition changes is not only time-consuming and costly, but makes it incredibly difficult to optimize resource usage in a way that meets performance requirements in a cost-efficient manner. As a result, services can fail because they don’t have enough resources available to handle the spike in demand. And operational costs can dramatically increase to ensure availability.
Centralized Governance and User Access Controls
Centralized governance allows admins to enforce policies across clusters, as well as applications running in those clusters. However, when cluster sprawl is left unchecked, it can introduce all kinds of complexities around access credentials, resource sharing, and security. And this problem only grows in complexity as more people on-board, off-board, change teams, and projects multiply.

How D2iQ Kubernetes Platform Simplifies and Accelerates Kubernetes Adoption
Enable Centralized Observability
Monitor Cluster Health and Performance
DKP enables centralized monitoring of any CNCF compliant Kubernetes cluster, including DIY clusters, other distributions, or Kubernetes in the cloud (EKS, AKS, GKE) from a single-view control plane. With integrated service monitoring, logging, and alerting capabilities, you can centrally review the health and performance of each cluster by region, availability zone, or cloud provider and see operational details, so that monitored threats are detected, and issues can be resolved before they escalate, thereby saving valuable time.


Provide Real-Time Cost Management
Identify Opportunities for Greater Cost Efficiency
DKP’s out-of-the-box Kubecost integration provides granular real-time visibility into how your resources are being spent across your clusters. By monitoring your Kubernetes spend across clusters, you can avoid overspend that may be caused by uncaught bugs or oversights. Organizations also receive dynamic recommendations on how to optimize their infrastructure spend, so you can avoid cost overruns and improve capacity planning according to service needs.
Automate Configuration Management
Configure Services Based on Intended Architectures
DKP provides an out-of-the-box cluster configuration manager, so that services and applications are correctly configured for admins and users, and specific versions are deployed to specific clusters. Admins have access to a centralized service catalog so they can quickly and easily deploy applications and complex data services to specific or multiple clusters, with governance. Further, by combining DKP with a service mesh, like Istio, organizations are empowered with a standardized way to discover, leverage, and deploy services across a variety of hybrid cloud, multi-cloud, and multi-cluster environments.


Enhance Application and Cluster Lifecycle Management
Improve Development Speed and Agility
DKP provides a single dashboard view and federated approach to application and lifecycle management. DKP comes with built-in GitOps capabilities that automate the delivery of applications. With continuous delivery to multiple clusters from a single control plane, you can ensure consistent upgrades, deployments, and security policies across any on-prem, cloud, or hybrid cloud environment with zero downtime.
Optimize Costs with Cluster Autoscaling
Scale Up and Down Based on Demand
DKP provides an autoscaling feature that works at the node pool level. Node pools can be configured to define autoscaling properties, such as the maximum and minimum size of the chosen pools. This enables you to easily scale down capability when it’s not needed, and add capacity when there is greater demand, resulting in lower operational costs.


Deliver Centralized Governance and User Access Control
Authorize and Authenticate Users Across Applications
DKP enables strong multi-tenancy capabilities that allow you to flexibly configure and manage users, roles, permissions, quotas, networks, and policies across any cluster or infrastructure. Role-Based Authorization (RBAC) can be defined centrally within DKP to control access to resources on the management cluster and a set or all of the target clusters. This approach gives you maximum flexibility over who has access to what resources, conveniently mapped to your existing identity providers’ claims.
Key Features and Benefits
Operational Dashboard
Provide instant visibility and operational efficiency into the Kubernetes landscape from a single-view control plane.
Centralized Observability
Gain deep insight into your Kubernetes clusters and applications with open-source metrics leveraging Telegraf, Prometheus, and Grafana.
Granular Cost Control
Drill down into cluster costs in real-time with an accurate and consolidated cost management across your cluster landscape.
Lifecycle Automation
Ensure consistent upgrades, deployment, and security policies for both infrastructure (through CAPI) and applications (through FluxCD).
Service Catalog
Quickly and easily deploy applications and complex data services from a centralized service catalog to specific or multiple clusters, with governance.
Cluster Autoscaling
Save operational costs by scaling down capability when it’s not needed, and add capacity when there is greater demand.
Service Mesh Integration
Add advanced networking capabilities, such as multi-cluster and cross-cluster service discovery, load balancing, and security across a variety of hybrid, multi-cloud, and air-gapped environments.
Governance Policy Administration
Meet the requirements of security and audit teams with centralized cluster policy management.
Centralized Authorization and Authentication
Enable single sign-on (SSO) across an organization’s cluster footprint and govern authorization with RBAC and Open Policy Access to enhance security and reduce risk.
Kubernetes Adoption Customer Success Stories:
Thank you. Check your email for details on your request.